Hack The Box is a well-known penetration testing platform and its challenges are often written about. Many blogs provide write-ups of the individual challenges showcasing the brilliantness of the author. I will write about the challenges that surprise me, such as the ID exposed challenge.
I found this challenge to be fairly difficult, not because of some difficult mathematical calculation, but because it’s based on an individual’s familiarity with how Google accounts function.
The ID Exposed challenge is in the OSINT category. The challenge description is:
We are looking for Sara Medson Cruz’s last location, where she left a message. We need to find out what this message is! We only have her email: saramedsoncruz[@]gmail.com
We have to find the last location of Sara using her Google account. Simple right? If you are familiar with Google accounts than this challenge is easy, in my case it took some time. After a few articles on Google accounts I discovered that most accounts have a unique identifier. For example, a user can have his Gmail account set as firstname+lastname[@]gmail.com and his YouTube channel as firstname2020. Using a unique identifier in the back-end would be handy.
Retrieving Sara’s Google ID
There are several methods to find a users ID. The quick and easy method is to create a new contact and fill it with Sara’s information. Using the developer tool embedded in your browser we can inspect the content of the web-page and find the user-ID.
Most user-IDs start with either 10 or 11. After digging around in the source code of the Google Contacts page we find the following:
data:["sara",[["c8256283197461861648",[null,[][],"117395327982835488254"
,null,["8256283197461861648"]
Photo Albums and Google Maps Reviews
With the User ID in hand, requesting Sara’s photo albums or maps reviews is a simple as requesting a URL.
Photo Albums
https://get.google.com/albumarchive/{userID}
Requesting an album using Sara’s ID result in a 404 URL not found error. So, Google Maps it is!
Google Maps
https://www.google.com/maps/contrib/{userID}
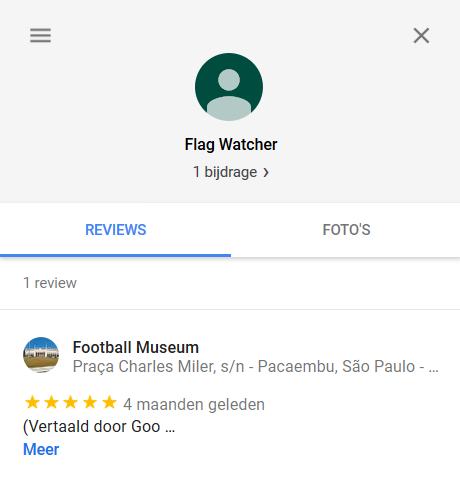
BINGO. Using the ID we find an account with the name: Flag Watcher. Flag Watcher has not uploaded any photos, however, there is one review. Read Flag Watchers review about the football museum to find the flag.